CONFIDENTIALITY
This principle focuses on preserving the privacy and confidentiality of information, ensuring that only authorized individuals or entities have access to it. Confidentiality measures include access controls, encryption, and secure communication channels.
INTEGRITY
Integrity refers to maintaining the accuracy, consistency, and trustworthiness of information. It involves protecting data from unauthorized modifications, ensuring its completeness and accuracy, and detecting any unauthorized changes or tampering.
AVAILABILITY
Availability emphasizes ensuring that information and resources are accessible and usable by authorized individuals whenever they are needed. This involves implementing measures to prevent service disruptions, downtime, and unauthorized denial of access. Redundancy, disaster recovery planning, and fault-tolerant systems are examples of techniques used to maximize availability.
Portfolio
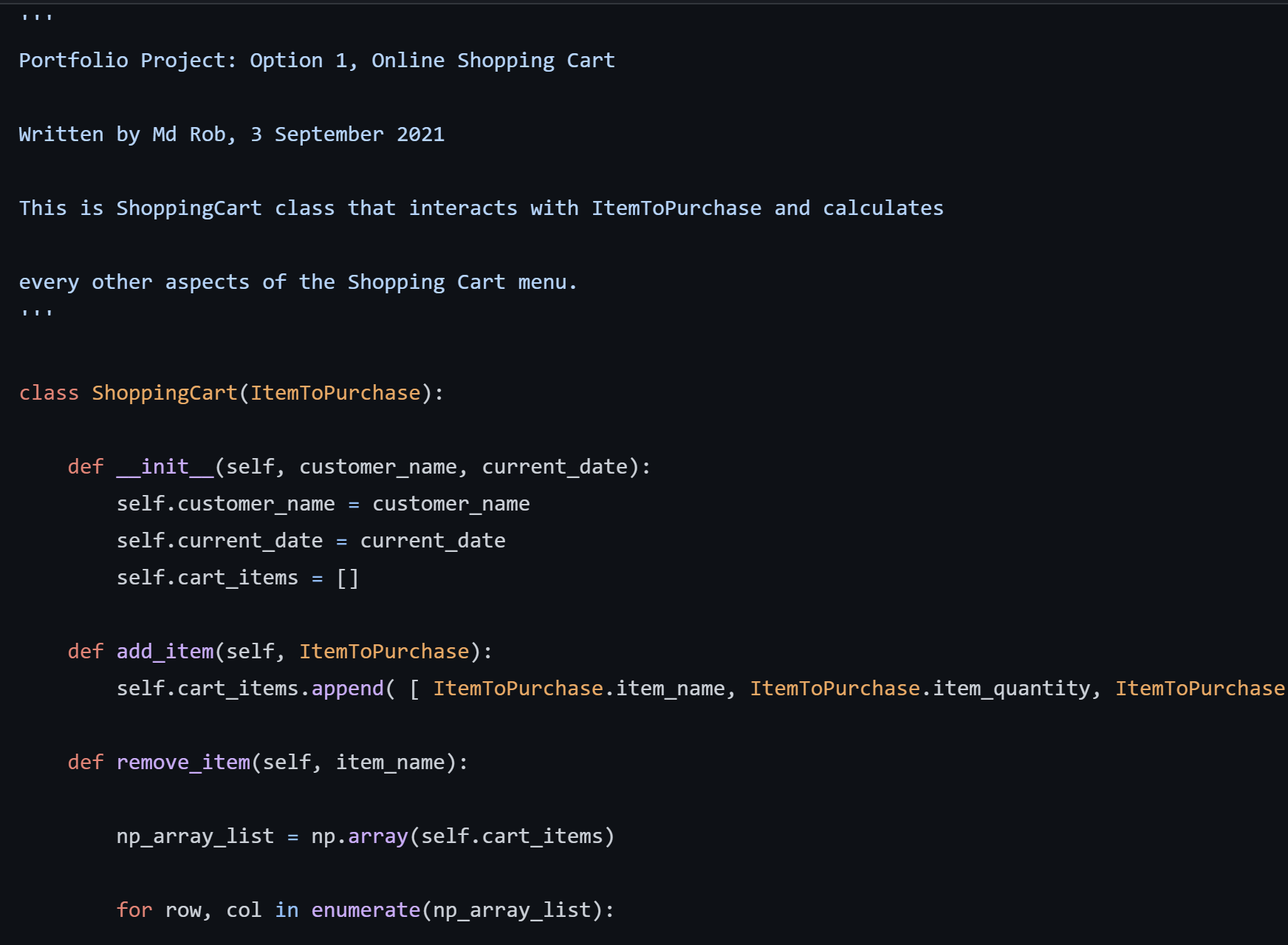
Item To Purchase
There are two classes. ItemToPurchase and ShoppingCart. Both classes are used to create a menu system using object oriented programming.
Deaths In Cstody
I have worked in a team environment to analyze deaths in custody data. The raw data was in csv format and we’ve tilized sql queries, pandassql library.
Bduget Analyzer
I have created a budget analyzer in python that used object oriented programming and database knowledge to analyze a month budget.
Security and Risk Management: Focuses on establishing and managing security governance and risk management frameworks, as well as understanding legal and regulatory issues related to information security.
Asset Security: Covers the protection of information assets through asset classification, ownership, and handling, as well as implementing appropriate security controls.
Identity and Access Management (IAM): Focuses on managing user identities, authentication, and authorization, as well as implementing controls for user provisioning, access control, and identity management lifecycle.
Security Assessment and Testing: Covers the planning, execution, and management of security assessments and tests, including vulnerability assessments, penetration testing, and security control validation.
Security Operations: Involves the establishment and management of security operations to detect, respond to, and recover from security incidents, including topics like incident management, disaster recovery, and business continuity.


CASE STUDY
Quest For Success
According to the book “7 Habits of Highly Effective People”, study shows that, successful people do not do things differently but they manage and execute around priorities. Mr. Covey illustrated a time-management matrix, that explains the difference between successful and not so successful people.
PERSISTANCE/HARDWORK
Persistence is the key to success.
MISSION
My mission is to secure critical & non critical information systems.
VISSION
Solving most complex cyber security/information system issues that has positive impact on people’s life.
VALUES
Integrity, service, wisdom, Honesty, respect others, care, love, empathy, sympathy, self-respect, self-commitment, excellence, and service.
What are you waiting for!
Testimonials
I’ve known Md A. Rob since 2012. He has always impressed me with his ironclad work ethic, focus, and goal-oriented nature. It has been a true privilege to watch his academic skills and passion grow nearly exponentially over 3 years at ELLIS, and then in the huge leap that he took to Clarkson, … Abdur Rob is a multi-talented, multilingual, super-dedicated, intelligent young man who is highly adept at adapting to new situations and environments. He possesses an admirable love of learning and is a great team player with others from a wide variety of linguistic, racial/ethnic, socioeconomic, and academic backgrounds.

J. Heyman
Author, Without a Margin for Error: Urban Immigrant ELLs in STEM
Md Rob is a man of dignity, respect, and punctuality. He always lives up to his words despite difficulties. We started college in the same year but on a different campus, he always brought up ideas and skills from his campus and shared them with me. I used to look forward to having a conversation with him related to the software industry and futuristic technologies. The best part about Md is the consistency and perseverance where he sticks to something until it’s done. He made it to Georgia Institute of Technology with his hard work and dedication towards technology while being a full-timer at work.

M. Alam
Artificial Intelligence Researcher | 3D Printing Engineer | Associate Software Engineer
I have had the pleasure of working with Abdur Rob for several years and on multiple projects in the fields of Computers and Communication Technology… improve his skills and range of knowledge. He is a quick learner and, … knows when to ask questions and how to seek out and implement solutions for the new problems/challenges.. His solid understanding of computer science principals and fundamentals was very apparent in his ability to quickly pick up the PHP language, and … aspects of our web-dev projects, despite coming onboard without much experience in PHP and the WordPress CMS…

C. Wenrick
Founder, Developer, & Project Manager with GMCT, Tech Teacher/Trainer, Technology Researcher, Instructional Designer
Latest from blog
How I Have Got Admitted Into GA Tech OMSCS Program?
Disclaimer: I can’t guarantee this will get you accepted for the Online Masters Computer Science (OMSCS) program. I can only speak for myself, what helped me to be admitted at[…]
Read moreGA Institute of Technology Statement of Purpose (SOP)
Masters in Computer Science Complete SOP Specialization in Computational Perception and Robotics I plan to do research in the field of computer science to make faster and more effective human[…]
Read moreAnalog to Digital Converter (ADC)
● Designed & implemented a digital system with Nexys4 board to communicate with I2C chip in VHDL ● Developed systems with standard integrated circuits; VHDL architecture, Finite State Machine ●[…]
Read moreContact me
Please fill out this form, I will get back to you, as soon as possible.